Episode 1029 (list of episodes)
NSA Whistleblower Bill Binney, and His Ordeal
William Binney on the Tom Woods Show
1 November 2017
... designates phrases that I (J. Gruber, being not a native English speaker) was not able to transcribe.
I also added notes in [ ], the links and the tables (about ThinThread and Pretty Good Knowledge).
Tom Woods: I am talking to the fascinating Bill Binney today, who is a cryptanalyst, mathematician and former highly placed intelligence official with the National Security Agency (NSA). During his carreer he received the Meritorious Civilian Service Award. He then became a whistlblower, who resigned on October 31st 2001 after more than 30 years with the agency. The following year he joined with a coulple of colleagues in asking the US Defense Department Inspector General to investigate the NSA for allegedly wasting millions and millions of dollars on Trailblazer, which is a system intended to analyse mass collections of data carried on communications networks such as the internet. Bill had been the inventor of an alternative system [ThinThread] and we'll talk about that, but since then he's become quite prominent as an opponent of NSA methods. He is now the subject of a brand new documentary that we'll talk about.
He's a very important guy, a very interesting guy, and I'm glad to welcome him to the show. Bill, thanks for being here!
Bill Binney: Well, thank for having me, Tom.
TW: I have this desire, as a host, never to bore the guests. Certainly I don't want to bore the audience - but I don't want to bore the guest with questions he's answered a million times. But unfortunately, Bill Binney, you are one of the souls who is destined to repeat his story many many times, indeed. So, I'm afraid I am indeed going to start there, but eventually I want to get to Russia. I don't want to leave the conversation without that tie to current events. But I do want to talk about your background because you and the NSA have rather an interesting carreer together.
Not only that, I just discovered this documentary about you called "A Good American" that I haven't seen, but I'm dying to see. I was actually wondering if I could show my kids this documentary without spooking them and making them terrified all the time. Could you give me some guidance on that?
BB: No, I think it's a good idea to show it to your kids so that they can begin - I think it helps inspire thinking, at least I hope it does, for people to start to think about what is going on, and not just absorb it from high up, like the White House or all of that, without any thought behind it. I always say: democracy is not a spectators sport. You have to participate, and in order to do that it requires thinking, not just absorbing and accepting as truth what people tell you. So, I really think it's a good idea for them - you should watch it first to see ... .
TW: Let's start with your carreer. What were you trained to do and what did you start doing for the US government?
timecode: 3:21
BB: Well, I got into intelligence in the US army in 1965. I was in there from 1965 to 1969. I did what they called traffic analysis, which is analyzing data and interactions between people and organizations. That's how it started and got me into looking at codes and cyphers and data systems and data.
TW: What was it that you were looking to do for the US government that, when the NSA started to do it, you had an objection?
BB: What I was doing with Ed Loomis in the SARC (SIGINT Automation Research Center) was putting together an automated process that would look at the entire world wide communication systems and decide what in there was important for analysts at NSA to look at, to start reporting on activities or threats from criminal organizations world wide or militaries or any leadership or anything. So the objective was to make sure that we got all of that data and not bury our analysts with other kinds of data, which they - back in the 1990s and before they had the capacity to do a lot of the collection of data - they were even buried back then. And so it was an effort to make them functional again.
|
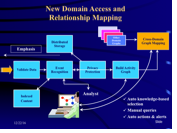
Fig. 1: Design of ThinThread
|

Fig. 2: Constructing subjects' network (see "Known" in Fig. 3)
|
|
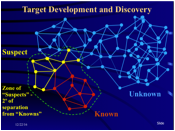
Fig. 3: Creating network of "Suspects" and discarding all further removed networks
|

Fig. 4: Pulling network of a suspect out from the global network
|
|
[The result was ThinThread, described in more detail in Sensing and Responding (in cache). Looking at the metadata coming in from the internet together with the communication data (yellow arrow on the left in Fig. 1: Aided by the analyst (arrows to and from analysts in Fig. 1)ThinThread generates the filter by automatically constructing sophisticated networks of connnections between people and their activities:
Fig. 2: It constructs communication pattern of people, anonymizing US citizens (example: node to the far right). Known terrorists are connected in the pattern "Known" (red in Fig. 3).
Fig. 3: ThinThread finds and connects "Suspects" (yellow in Fig. 3), i.e. persons connected via 1 or 2 hubs ("degrees") with "Knowns" and discards the rest ("Unknown", blue in Fig. 3).
Fig. 4: The analyst decides which part of the global networks he considers relevant, pulls it out and receives the corresponding communication content and its timeline.
In essence, any recognition works that way, regardless of circumstances and species. In order not to be overwhelmed by the amount of information, characteristic patterns in space and in time are sought and compared with previously encountered ones. The procedure is used by micro-organisms, between people, by the immune system, in our neural system, our mind: To regognize something, we compare the new pattern with ones we have found the most helpful ones in similar circumstances. Before we know the details, we say: "This looks like a book." In his model (Theory of Neural Group Selection, in cache). Gerald Edelman calls this "selection based on neural Darwinism".
For more details see also Friedrich Moser's film (or trailers of) "A Good American"]
|
- But what they [NSA] did was, once we had the capabilities [i.e. with ThinThread] to see into everything and it's like going what we wanted, they removed that filtering up front and just took in everything [all the data coming in from the internet]. That [filter] was the first thing they removed [when they took over ThinThread and transformed it into what they called Stellar Wind].
- We had built into that system also a method [box "Privacy Protection" in slide 24 of Sensing and Responding] of protecting the identity of people by encrypting their data, so that no one could tell who they were, and NSA analysts for example couldn't do what they called internally "love intelligence", where they looked into the data to see whether their lovers were cheating on them. They couldn't do that because they wouldn't be able to tell which encrypted data [Fig. 2] represented their lovers. So they removed that.
- And then the other thing: We had a monitoring system that was monitoring what was going on in the network when people came in to look at the data, so we could see what they were doing, where they went, how long they stayed and what they did while they were there. Since they didn't want any monitoring of what they were doing they removed that. And so they ended up being monitoring everybody.
That's what they [NSA] did to that program [ThinThread]. They distorted it totally [the code name of that stripped down version of ThinThread is Stellar Wind, Kurt Opsahl (EFF) "NSA Spying - How It Works"].
TW: Doesn't that lead from their point of view to information overload? I mean, from our point of view it's frightening that they have all this information. But when you have all that information how on earth would you be able to sort through it?
BB: That's the point: they can't, and that's why they're failing, and that's why the attacks occurred and they can't stop them.
TW: That raises a good question: Have they been able to point successfully to any nefarious activity they have been able to stop? Had they tried to point to anybody?
timecode 6:25
BB: They did, with the Leahy Committee, in that Senate Judiciary Committee. Keith Alexander, former director of NSA, claimed they had stopped, that the program had stopped 54 attacks. Then Senator Leahy asked him to prove it, and he couldn't prove any of them.
[quote added by J. Gruber from Jenna McLaughlin, "U.S Mass Surveillance Has No Record Of Thwarting Large Terror Attacks, Regardless of Snowden Leaks", The Intercept, Nov. 17 2015 (in cache) "... only 13 of the 54 cases Òhad some nexus to the U.S.,Ó Senator Patrick Leahy, D-Vt., said in a Senate Judiciary Committee hearing in October 2013. And they were not all terror ÒplotsÓ; a majority involved providing Òmaterial support,Ó like money, to foreign terror organizations.
Then-NSA Director Keith Alexander was forced to dial back the rhetoric, eventually saying only that the intelligence programs Òcontributed to our understandingÓ and Òhelped enable the disruption of terrorist plots.Ó
See also "Not all Plots, not all Thwarted" (in cache)]
TW: Does that put them on par with the TSA, then?
BB: I guess pretty much so :) I looked at it as a swindle. They kept telling us all the time you had to give up privacy for security, and it's been a lie from the beginning, and they knew it and perpetuated it because it meant they got a lot of money to perpetuate or build up their intelligence apparatus.
TW: What do you think is the primary problem? Is it that there is the potential for abuse? For instance, somebody who is politically unfashionable could have all kinds of compromising information about him in the hands of the government - where does the danger lie, so that the average person sees where the danger is.
BB: Let's put it this way: If you looked at what they did to the Tea Party. That can be deduced directly from this data, because the networking is all there for all the Tea Party people. Also any religious group trying to get association with ..., active in fiber 1C3 activity (?). The IRS also has a view into this data and that's how they got this information, I'm sure. Also Eliot Spitzer when he was going up to the bankers for the fraudy people in the 2007/8 crisis. They got rid of him by looking in his data and they also went after Jim Risen and Jim Rosen and the Associated Press, so much so that the press is basically no longer an investigative tool, it's functionally dysfunctional.
TW: Of course, these unfortunate things are going to happen. The best we can do is try to minimize them. But the fact is: We live in a world now where we have such a wrily enemy, who moves so quickly and their contacts are so instantaneous and swift that we don't have time for the old clunky system of the FISA court or whatever. We just need to have a system that's agile, that's on the spot, that's ready to go, and if we don't have that we're going to be vulnerable.
BB: That's also a lie. We had said back when we were there that we wanted to automate the requesting for a warrant. Which meant that we could do a could of couple of millions a day. So there was no need. That was also a false issue, a red herring.
TW: OK. Tell me about ...I want to know something about what happened to you personally. Was there actually a raid on your home?
BB: Yes.
TW: On what grounds?
BB: Well, It's fabricated. The FBI under Mueller, I might add, and the DOJ under Comey falsified statements to the court to get a warrant to do a raid on us. We pointed that out, wanted to sue them for violation of constitutional rights because of the lies they put into the affidavit.
timecode: 9:35
TW: Why were they targeting you in the first place?
BB: Because NSA wanted them to do it. We filed a DOD IG (Department of Defense Inspector General) complaint about NSA's corruption, fraud, waste and abuse, and the DOD-IG office found that everything we said was true and much more, and they reported that in their intelligence report (DOD IG 05-INTEL-03) titled Trailbalzer and ThinThread Requirements (alternative link). That was published in 2005, and they're keeping that under wraps since then. They don't want anybody to know about all this corruption going on.
TW: Can you describe the scene for, what happened at your home?
BB: About 12 agents with guns drawn came in, pointing guns at my son, my wife and me. It was basically an attempt at intimidation, because they didn't want us to talk about what we knew of the terrorist surveillance program and the violation of constitutional rights of every US citizen.
TW: How long did this go on?
BB: The came in at 9 o'clock in the morning and left at about 4 in the afternoon, something like that.
TW: Were they going through your papers and things?
BB: Oh, everything. They destroyed our business and took any electronic equipment we had, phones, emails, disks, computers, everything.
TW: These things were of course returned at some point?
BB: Only after we sued them. They kept it for 5 years, and so we did what's called a 41 (g) Return of Property Lawsuit [Federal Rules of Criminal Procedure - Title VIII. Supplementary And Special Proceedings - Rule 41. Search and Seizure - (g) Motion to Return Property] because they are required by law to tell us after they confiscate, within 60 days they have to tell us what material they are going to keep and what they'll return, and then didn't that for 5 years. So they violated the laws, and so we did a 41 (g) lawsuit and won, by the way. We set a precedent by doing that. We represented ourselves pro Se, and we made them look like silly fools in the court room.
TW: I wish we had a video record of that. Did you have any incling that this raid was about to happen? Did it take you completely by surprise?
BB: Actually the court still has the audio of that trial. It's the Federal Court in Baltimore.
TW: Did you have any inkling that it was coming?
BB: Actually not. They had been asking me about ..., 'cause this was after the New York Times exposure of the warrantless wiretapping. They called me in. I'd been talking to them several times - i met with them 3 times before the raid, and told them everything I could remember, and they obviously - we actually found out later that the Department of Defense's Inspector General gave our names as likely candidates to them, because we filed that report to the DoD IG's office. Which [the filing of the report] is what you're supposed to do by law. Also it's a requirement for working for the US government. You are required to report fraud, waste, abuse and criminality.
TW: Can you, just so that we can get this all straight this in our mind, just go over the timeline with us of exactly when you did that and when this raid occurred? At least just those two dates, roughly.
timecode: 13:00
BB: We filed the complaint in September of 2002, and the raid occurred in 26 of July 2007. The Inspector General's Office didn't give our names till after the 2005 New York Times report.
[On 27 February 2001 (i.e about 7 months before 9/11) NSA approached Qwest to get all of their customer information. The point is, 3 - 4 months before that, in November 2000 ThinThread was functioning, thus could have been applied to the search for terrorists. Instead, US government used 9/11 to intimidate Congress into approving the government's mass surveillance programs that are totally ineffective tools against terrorism on the one hand, and on the other hand effective tools for
"social control, diplomatic manipulation and economic espionage. Ultimately, they are about power, about gaining influence relative to other groups within our society and around the world (source b).
... In the United States, at least, ... the funding of it comes primarily from taxes in your local community, but the public hasn't been getting a vote on this .... We are trying to change that now. This is one of many efforts that I [Edward Snowden] am involved in. More importantly, our civil rights organizations, such as the American Civil Liberty Union (ACLU) [with #Take CTRL, Community Control of police surveillance], Electronic Frontier Foundation and other organizations, both in the United States and international, around the world, are starting to recognize 'ok, we can disagree about where we want to draw the lines, how surveillance authorities are being used in our society'. .... Ultimately, we are not a democracy if we are not getting a chance to guide these decisions." (source a)
Sources:
]
TW: You were in the intelligence community, you were appalled at what you saw going on at the NSA ...
BB: ... these were all impeachable activities, by the way, it's all a direct violation of the Constitution.
TW: How many people, did you feel comfortable talking to you colleagues about this?
BB: Sure.
timecode:13:34
TW: .. and you must have had some who felt the way you did.
BB: Oh, yes. Some of them retired and got out of the place when I did. So, there were a number of people inside NSA, went to talk to the Inspector General inside the NSA, and then they were visited by the FBI and basically told to basically be quiet.
TW: Did some of them remain quiet?
BB: Most of them did. They were afraid of losing their jobs or even of being indicted or something. That's what they were threatening.
TW: Given that -as you say- some people resigned over this or one way or another they left, what does that say about the composition of people working at the NSA today?
BB: They are afraid, and they are basically, under the Myers Briggs they're ISTJs, sensing, thinking and judgemental people, so basically they are the kind of audience that can be easily threatened.
TW: But also I would think at this point if you were going to work for the NSA in 2017 you know what they are up to, right?
BB: Yes. right now, that's right.
TW: So how did your name, your individual name, given that there are other critics, get to be associated with this. Did you begin speaking out publicly?
BB: No. In fact, we had done everything inside channels, with the intelligence communities or with the Inspector Generals of the Department of Defense and also of the Department of Justice.
TW: But yet today, you are in demand. I've seen you on different programs to speak around the country. So, how did you become rather a celebrity in this area?
BB: Well I just got out there and told the truth. I guess the truth is kind of rare these days. And everytime I did, well, people wanted me to come and give other talks. And I did, as much as I could. In fact, the latest ones I gave with Arjen Kamphuis in Vienna
[Binney@epicenter.works, berwachungspaket bei Begutachtung durchgefallen, und Ex-Cheftechniker der NSA warnt vor berwachungspaket, 11.8.2017]
talking against this bulk big data that they were also advocating. A very similar bill to the British IT-Bill and what NSA has been doing in secret from 2001 on, kind of authorized and retroactively made it legal. And we talked against that and finally the supreme court in Austria ruled it unconstitutional. And also the parliament voted the bill down. And so that's the first country to start doing something positive in the right direction
["berwachungspaket gescheitert: Wir rufen zum Schulterschluss fr Sicherheit statt berwachung auf", 1.9.2017].
TW: Just before I forget: You say some people didn't want to lose their jobs and so may be they thought the best thing was to just keep quiet ...
BB: ... but they also saw what was happenig to us. They saw that people were going to be attacked, you have to defend yourself against the government. That really can basically bankrupt people.
timecode 16:28
TW: Yes, and ruin their future prospects. So, what did you wind up doing, once you left this field?
BB: Well, after I retired I went directly to the House Intelligence Committee net. Of course got things started then. The staffer on the House Intelligence Committee brought it up with [Porter] Goss, who was the chair, and Pelosi, who was the ranking member, and they both told her that she should go see General Hayden, who was the director of NSA at the time. What she didn't know was they'd both already agreed on October -the briefing they got of this program- back in October 2001 they both agreed to it.
Now, this is the House of Representatives that's supposed to represent us and they also took an oath to defend the Constitution, and these are grounds for impeachment, they never followed through. The reason they didn't - that's why Pelosi said "impeaching George Bush is off the table", because she was involved in agreeing to the program, so if she wanted to say "I want to impeach you", then he would say "you have to impeach yourself because you are part of this".
TW: What was your thought when you discovered that the New York Times had known about warrantless wiretapping and sat on the story for maybe a year and a half?
BB: Well, I thought it was disgraceful. I mean that tells you what's happening to our news and reporters and all the news agencies we have, because they're all being threatened, and you can just see how the government can manipulate them. They can threaten them with grand juries as with Jim Risen and so on. So, even they are getting the message. They are basically staying quiet and saying nothing except what the administration is telling them. The administration in here includes the agencies of the government, like NSA, FBI, CIA.
TW: I want to ask you, before I ask you about Russia, about this brand new documentary about you, called "A Good American". How did that come about and what do people learn in it?
BB: It started by a phone call from Fritz Moser, the director of the movie, in August of 2013, I believe it was. Then he said he was interested in finding the background on what this intelligence was all about, the bulk acqusition and spying that came out from Edward Snowden's material. He said he saw me as one that was there when [he followed] the thread back, he didn't know how much of a thread I had on that. He said "would you like to come over and we could discuss this?", which I did in October of 2013, and then from thereon he said "Gee, this is really a great story!", and he wanted to film it and put it in a movie. From thereon we started doing the movie.
timecode: 19:11
TW: Apparently the documentary claims that the ThinThread system, which may be you might comment on, would have prevented the September 11 attacks. Can you elaborate on that?
BB: Yes, in fact that was basically proven by Tom Drake after we left NSA. He was finally given an opportunity to run the entire NSA database through the ThinThread program. And then it picked out all kinds of material that they didn't even know they had, including
- the dispersal patterns of people after the attack and also
- warning of the attack, plus, I think,
- the date and the time also in that data of the attack before the attack. Of course it picked up
- the calls from all the travellers (?) that came in from Kuala Lampur and to San Diego. They picked up
- all the calls that they made back to the Yemen Al-Qaeda facility.
All that material was pulled out by ThinThread and they didn't seem to know about it.
TW: That's rather an indictment, too, expecially because the claim seems to be the more intrusive we are, the better the intelligence results will be.
BB: You see, the problem here is the people in charge in these agencies are mentally warped. They think collected data is intelligence. It's only intelligence once you understand it, and if you collect so much that you can't understand it, then you fail. That's what's been happening.
timecode: 20:38
TW: You've continued to comment on current events over the years, and one that is of particular interest to me involves this whole question of Russia. We just had these indictments handed down over the past day or so. I'm interested in this so-called assessment from January of this year. The claim is that the Russians hacked into the DNC, got their emails and then - this is the key thing- turned them over to Wikileaks. Now you have been, I guess, involved with the Veteran Intelligence Professionals for Sanity (VIPS), which is a group named that I've always loved ever since they started it, and you guys did some work that contradicts this so-called assessment. First of all, in the assessment, what was the evidence - I suppose this is a loathed question- what was the evidence they brought forth to this claim
BB: No, there wasn't any. It was just [they said] "we have high confidence they did it", that's all. It was a manufactured assertion without any factual base. The only evidence we really found, we really looked at and analyzed, was in the Guccifer 2 attack, 5th of July, 2016. He announced publicly on the 4th that he was going to get more data, on the 5th this download occurred, and on the 6th he said he got more data ... July last year.
- So, we looked at that (in cache) and it turned out basicaly that within a 14 minutes period there were 2 segments of transmissions for a total of 87 seconds.
- He downloaded almost 16 Gbits of data during that period.
- The high speed was 38 MB per second, which is close to 38 MB x 8 bit/B = 304 Mbits per second.
The point was: all the people we had that were technically smart about the network etc. said that this is not possible to do. The network can't support that kind of transmission at that rate. But it does - the rate came across at the standard rate for a download to a thumb drive.
It made a lot of sense to me because of the time I was buying 16 Gbits thumbdrives and if you downloaded almost 16 Gbits you don't want to do it all on one thumb drive, because you might miss something. So you get to split it off on two. That's why it came in 2 segments in my opinion, simply because he divded the data into two parts and took the first part down in the first segment and took the second part down on the second segment on 2 separate thumb drives. Thus, put one in, download, take it out, put one in, find out where you left off and start downloading from there. That's why we had that time gap in the middle, in my view.
timecode: 23:27
TW: In light of what you found looking at all this stuff, what is your working hypothesis as to what happened?
BB: It was a local download by somebody who can get into the DNC network, because you could download it at that rate on a local network, but you can't send it across the internet.
We tried, actually physically tried, to do that. We tried to move out a Gbit of data and see how fast can you move that across the Atlantic to somewhere in Europe. The fastest speed we got was between a data center in New Jersey and one data center in the UK, and that got up to 12 MB/second. That's roughly 1/4 the speed necessary to send the data itself, without any overhead. If you put the overhead on, it's probably about 1/8 the capacity you'd need to get that transmission across the Atlantic to somewhere in Europe. As we went further, into Eastern Europe, e.g. to Albania or Belgrade, the whole system degraded basically to dial-up, I guess, something that you couldn't even consider was worth even a try to download in those locations.
TW: Is there anything to the claim that the -I'm so tech non-savy with this ... - was there some attempt made to make it appear as though this activity had Russian origins.
timecode: 24:56
BB: Yes, they used the templates, plugged data into templates, they put data in there that made it appear to be cyrillic, for example, names, they tried to associate it with the Russians, but that was all a ruse and a fake. It was pretty clear to our people who were looking at it that that's what was going on.
TW: Would you say then that the Russians had no fingerprints anywhere, on anything? What do you say about the whole question of Russian hacking or involvement in the election?
BB: We haven't been able to find any evidence that they did anything.
["Au§erdem kenne ich den ehemaligen Diplomaten Craig Murray, der von einem DNC-Angestellten den USB-Stick mit den Daten erhielt und diesen an Julian Assange von Wikileaks weitergab.persnlich"
"Besides, I know the former diplomat Craig Murray, who obtained from a DNC employee the USB stick with the data and passed it on to Julian Assange of Wikileaks"
Source: "Sie wollen einen neuen Kalten Krieg - Ex-NSA-Chef Bill Binney ber seine Entscheidung, Trump zu whlen und wie eine zielgerichtete berwachung aussehen kann.", Interview: Anna Goldenberg, Falter 33/17, 20 (2017)]
TW: And yet, we just had these indictments handed down, as you and I are speaking it was just within 24 hours, and it's three people, but what's the significance of these indictments, as far as you have been able to determine?
BB: Whar they are being accused of, they did from 2006 to 2012, well before the election campaign and so on. So, when it comes to the campaign, I don't know what the association is. When it comes to money and so on, manipulating money, I think that's the issue there.
timecode: 26:09
TW: So, why do you think, there is this campaign to taint the Trump campaign with Russian influence and to demonize the Russians? Where is it coming from, and what's the motivation?
BB: I think the motivation is from politicians. Trump is not a politician. You can't have somebody becoming the president of the United States that's not a politician and succeed and make them look pretty silly, as he has been doing. I think he's made them economically look like amateurs. That's one of the things they want to avoid. They don't want someone from outside the political arena to look really good while they look really bad. That's their fundamental, founding motivation, I believe. Other than that, they want to make this administration impotent and not being able to do anything and that it will succeed that way politically in the votes in the next election. It will satisfy their need not to look bad.
TW: Here is my last question for you: When you hear the phrase "Deep State", what do you think, what does that mean?
BB: The Deep State to me, I mean I look at it as a shadow government, which is the intelligence community and their associated afiliates in the US government. Deep State means all of the corporations, banks, and technical companies that are part of putting up this empire and dependency on government spending and government contracts.
TW: I had Ron Paul on the show last week, and I asked him: "Why couldn't a really ambitious president come into the power and say to the heads of all these various organisations: "You are all dismissed. I'm appointing people who are not going to be running a shadow government, but who are allies of mine and who are going to clean house there and that's the end of this. The elected people are in charge once again." What would stop him from doing something like that?
BB: Only the will to do it. That's what he should do in my view. But if he doesn't have the will and the backing of his cabinet, for example, to do that kind of a thing, then he probably wouldn't.
TW: Of course, there is Trump's big problem: He's so ideologically confused in my opinion, not that he's a smart guy in his own way. But he's not ideologically consistent. I wouldn't say he has a political philosophy or anything. He's surrounded himself by people who by and large are really not sympathetic to him. It's completely bizarre to me. The Democrats don't do that. They are all going to be absolutely loyless (? disloyal?) to their nominee [appointee?]. He's surrounded by sharks, and that's of his own doing.
BB: Yes, that's part of the problem with every president. I mean, the bureaucrats are still there, no matter what the president is. I call them the "pretorian guard". They kind of determine who the emperor is and what the emperor does. I mean, that's why Senator Schumer was warning President Trump that attacking the intelligence community is a very dangerous thing. They have many ways of getting back at you. What he is doing, he is experiencing some of this now.
timecode: 29:33
TW: And yet, our kids in school continue to learn ... how a bill becomes a law, what the textbook operation of the US government is. I'd much rather have my kids know the actual operation of the US government. We read about [it in] the papers, a lot of times we don't know about.
BB: I think, Goethe captured it many years ago, in a statement he made. He said: "None are more hopelessly enslaved than those who falsely believe they are free." [Bk. II, Ch. 5; source: Die Wahlverwandtschaften, Hamburger Ausgabe, Bd. 6 (Romane und Novellen I), dtv Verlag, Mnchen, 1982, p. 397 (II.5)].
|

Website: Pretty Good Knowledge
|
We are on a mission to help organisations achieve control and confidence about the knowledge and insights they extract from the ever-growing sources of data. Technology capabilities, legal considerations, moral dilemmas and consumer preferences are changing at a pace which requires a new way of thinking to comprehend. Your people, your solutions and your partners need to constantly improve in order to solve the problems of today and lead the market with the opportunities of tomorrow.
KNOWLEDGE by design: Organisational and process methodologies to improve your data management maturity and analytics capabilities.
PRIVACY & SECURITY by design: Technical architectures and tactics to provide increased security and privacy compliance across your organisation.
SOLUTIONS by design: Increasing value from our applied experience with solutions your organisation is designing, developing or implementing.
|
TW: Before I let you go, tell me about the website you and I were talking about before we started recording that you are working on now.
BB: Actually, Kirk Wiebe and I, we've started a company with partners in Amsterdam, The Netherlands, to resurrect and do the kinds of smart things we thought we do with data back in the 1990s, because this government and the Deep State as well as the shadow government didn't want us doing that here. So we're over there doing this.
TW: And what is the website?
BB: The name of the company is PGK, for Pretty Good Knowledge. The website is prettygoodknowledge.eu
TW: .I think I have more or less kept your ordeal in terms of the time I would keep you, and I'm grateful to you, because it was a great conversation. I know other people like me are now going to want to go on a Binney binge online. So, thanks so much.
BB: Thank you!
Links provided by Tom Woods
Subscribe to the Tom Woods Show: https://itunes.apple.com/us/podcast/t
Version: 15 February 2018
Address of this page
Home
Joachim Gruber




