
Glass House,
Status Floor, mid July 2013
Video: Gerhard Richter, Abstrakt ab 2005
Audio: Anton Bruckner - Symphony no. 8 - III (1/4), Bernhard Haitink conducting the Royal Concertgebouw Orchestra Amsterdam.

Glass House, |
Video: Gerhard Richter, Abstrakt ab 2005 |
Would politics and media continue to disregard and misinform the public when individual citizens have more power by owning a sizeable part of the electricity generating capacity?
Or: Do Conservatives and Socialdemocrats stifle photovoltaic electricity generation to avoid creating possible electricity "Smart Mobs" (a new form of strike)?
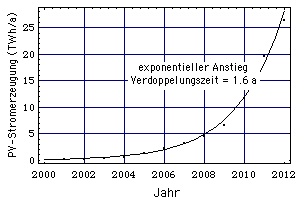 |
German annual photovoltaic (PV) electricity generation doubled every 1.6 years.
As PV energy production doubles every 1.6 years, in 5 - 6 years individual persons would provide Germany with 20 % of its electricity. This gives them political power. |
The SRU warns explicitely against such misinterpretations.
Both effects are not do not reflect the subsidies for the renewables. Wrong indicators can lead to wrong reforms that can slow down the buildup of renewables and endanger the energy transition ("Energiewende").
Therefore the SRU recommends a better indicator with which to judge whether or not renewables become more cost effective. Suitable would be the EEG-Umlage for newly built renewables. In addition, a comprehensive economic cost definition should be used. It has to compare the total costs related to renewable energies with the costs -also the external ones- that originate from the switch from fossil to renewable energy (difference costs).
3. Films I uploaded onto Youtube in 2013
Book: Dieter Forte, Director: Peter Patzak,
Actors: Ernst Schröder, Joachim Dietmar Mues, Ulrich Faulhaber, Ludwig Tiesen, Eberhard Busch, Marie-Luise Etzel, Gert Burkard, Ilsemarie Schnering,
Production: Peter Schulze-Rohr,
Production of the Südwestfunks Baden-Baden, 1980
Part 1 of 6,
Part 2 of 6,
Part 3 of 6,
Part 4 of 6,
Part 5 of 6,
Part 6 of 6.
Book and direction: Carlheinz Caspari,
Cast (Characters): Karl Walter Diess (Hermann, the Professor), Christian Berkel (Dick, son of the Professor), Elisabeth Ackermann (wife of the Professor), Franz Rudnick (Egon, constructor), Marianne Kehlau (Karin), Jörg-Peter Falkenstein (Kurt, personal referee of the Professor), Günther Dockerill (Achim, friend of the Professor), Ursula Vogel (Mrs. Zogelmann), David Anchondo (guitarrist), Helga Bammert, Charlotte Bremer-Wolff, Jörg Christiansen, Heinz Dohmes, Günter Eisel, Rolf Jahncke, Wolfgang Kaven, Klaus-Hagen Latwesen, Thomas Meinhardt, Antje Mestern, Joachim Rake, Antje Reinkem, Charlie Rinn, Monica Rosenquist, Nikolaus Schilling, Günter Schulz, Uwe Steffen, Hans Peter Sternberg u.a.,
Production: Dieter Meichsner,
Norddeutscher Rundfunk Hamburg, 1979
The politically committed Carlheinz Caspari pictures the socio-political circumstances of the late 1960s and early 1970s in West Germany, a psychogram of a part of the society at the time. The film is a search for a lost time, accommodated in the expression "Beyond Sweden". It reminds me of Raul Ruiz's film "Le temps retrouvé" (Times Regained).
Details:
The protagonist (Professor) is loosely shaped after the charismatic, influencial economist, social-democratic minister and long-time companion of Willy Brandt, Prof. Karl Schiller. His ideas (e.g. formulated in his Schnellbrief, in which he describes an increasing public debt as not justifiable in terms of stabilization politics) pervade a major part of the film, partly as antithesis to the indifference towards their own country as shown by others in the film. Schiller summarized his engagement for Germany in a letter he published when leaving the Brandt administration ahead of time: "Government has the obligation to look beyond its own horizon given by the election date and tell its people in time what has to be done and what has to be demanded. This my several times recommended strategy has not even been discussed, much less accepted." (Source: Karl Schiller, "Letter of resignment of the Minister of Economic Affairs and Finances, 2 July 1972, Digital Archive, Marburg")
Part 1 of 5
Part 2 of 5
Part 3 of 5
Part 4 of 5
Part 5 of 5
Stage Director : Fritz Kortner,
Film Director: Marcel Ophüls,
Thomas Holtzmann (Clavigo), Rolf Boysen (Carlos), Friedhelm Ptok (Beaumarchais), Krista Keller (Marie Beaumarchais), Kyra Mladek (Sophie), Hans Häckermann (Guilbert), Knut Hinz (Buenco), Horst Reckers (Saint George), Hans Irle (Diener des Clavigo)
Deutsches Schauspielhaus Hamburg, Norddeutscher Rundfunk, 1970
In his first television interview since he resigned from the National Security Agency over its domestic surveillance program, William Binney discusses the NSA's massive power to spy on Americans and why the FBI raided his home after he became a whistleblower. Binney was a key source for investigative journalist James Bamford's recent exposé in Wired Magazine about how the NSA is quietly building the largest spy center in the country in Bluffdale, Utah. The Utah spy center will contain near- bottomless databases to store all forms of communication collected by the agency, including private emails, cellphone calls, Google searches and other personal data. Binney served in the NSA for over 30 years, including a time as technical director of the NSA's World Geopolitical and Military Analysis Reporting Group. Since retiring from the NSA in 2001, he has warned that the NSA's data-mining program has become so vast that it could "create an Orwellian state". Today marks the first time Binney has spoken on national television about NSA surveillance.
This interview is part of a 5-part special on state surveillance (audio-cache). Click here to see segment
- National Security Agency Whistleblower William Binney on Growing State Surveillance (Cache, Transkript)
- Detained in the U.S.: Filmmaker Laura Poitras Held, Questioned Some 40 Times at U.S. Airports (Cache, Transkript),
- We Don't Live in a Free Country - Jacob Appelbaum on Being Target of Widespread Gov't Surveillance, (Cache, Transkript),
- Whistleblower: The NSA Is Lying - U.S. Government Has Copies of Most of Your Emails (Cache, Transkript),
- More Secrets on Growing State Surveillance: Exclusive with NSA Whistleblower, Targeted Hacker (Cache, Transkript).
[all include rush transcripts].
In part two of our national broadcast exclusive on the growing domestic surveillance state, we speak with National Security Agency whistleblower William Binney and two targeted Americans: Oscar-nominated filmmaker Laura Poitras and hacker Jacob Appelbaum, who has volunteered for WikiLeaks and now works with Tor Project, a nonprofit organization that teaches about internet security. Binney left the NSA after the 9/11 attacks over his concerns about the agency's widespread surveillance of U.S. citizens. He describes how the FBI later raided his home and held him at gunpoint and notes there is still no effective way of monitoring how and what information the NSA is gathering on U.S. citizens and how that data is being used. Click here to watch part one of our special report. [Includes rush transcript]
Pt.1: Hedges and Binney on Obama NSA guidelines
Chris Hedges and NSA whistle-blower William Binney tell Paul Jay that there should be accountability, including the President himself, for the criminal practices used by the NSA against the American people - January 10, 2014
Pt.2: Hedges and Binney on NSA Policy
On Reality Asserts Itself with Paul Jay, Chris Hedges and William Binney answer the question: "What should the NSA policy look like?" - January 11, 2014
Thomas Drake, a former Senior Executive at NSA who was charged under the espionage act after he blew the whistle on waste and fraud and illegal activity at the intelligence agency, spoke at a March 15, 2013 National Press Club luncheon. Drake's event was part of the club's celebration of Sunshine Week, a national initiative to underscore the importance of open government and freedom of information.
Whitney Museum of American Art, April 20, 2013
Award-winning filmmaker Laura Poitras explores issues of war, justice, and power. Her current film trilogy, focusing on America post 9/11, documents the Iraq War, secret state surveillance, and the suspension of the rule of law in the "war on terror". Here, Poitras gives the floor to Jacob Appelbaum, computer security researcher, privacy advocate, hacker, and human rights activist, and Bill Binney, National Security Agency whistleblower. Appelbaum and Binney discuss domestic surveillance and the ways in which technological innovations have allowed for increasingly ubiquitous access into what was once private information. (Source)
30th Chaos Communication Congress (30C3), Hamburg, 22:00 Uhr, 29 Dezember 2013
30th Chaos Communication Congress (30C3), Hamburg, 11:30 Uhr, 30. Dezember 2013
Jacob Appelbaum, Judith Horchert, Ole Reißmann, Marcel Rosenbach, Jörg Schindler und Christian Stöcker: Neue Dokumente: Der geheime Werkzeugkasten der NSA
"Die NSA hat eine geheime Abteilung, die Spezialausrüstung herstellt: Spähsoftware für Rechner und Handys, Mobilfunk-Horchposten, manipulierte USB-Stecker und unsichtbare Wanzen. Hier sehen Sie Auszüge aus dem hausinternen Bestellkatalog der Abteilung ANT - Preise inklusive."
Jacob Appelbaum: Art as Evidence - Keynote, transmediale 2014, Berlin
30th Chaos Communication Congress (30C3), #5415, Hamburg, 12:45 Uhr, 27. Dezember 2013
In diesem Vortrag soll das Konzept des tiefen Staates anhand der bundesrepublikanischen Geschichte aufgezeigt werden. Rechtliche Aspekte kommen ebenso zur Sprache wie der hohe Grad der Militarisierung und das Ausmaß der Überwachung. Auch die historischen Konflikte zwischen paranoidem Rechtskonservatismus und bürgerlichem Widerstand finden Erwähnung. Ein Ausblick soll die Debatte über die Zukunft des tiefen Staates nach draussen tragen.
Vortragszeitpunkt 32:50: "Was passiert, wenn wir eine Personengruppe haben, die demokratisch legitimiert eine Veränderung herbeiführen möchte, die aber bereits im Vorfeld in einem Maß ausgeforscht wird, dass sich diese staatlichen Strukturen gegen sie wenden können. ... Ich würde gern in den Dialog mit Euch eintreten, und mit Euch herausfinden, wie Eure Sicht ist auf diese Infrastrukturen. Denn wir haben diesen Umbau vor uns, das wird kommen, das ist das, was die aktuelle Regierung tun wird als Argument zur Beschwichtigung der Bevölkerung gegen die Überwachung aus dem Ausland. D.h. wir werden irgendeine Form von Konzentration von Datenverkehr im Inland haben, wir werden weniger Austauschpunkte haben, wir werden bei der Gelegenheit vermutlich eine Harmonisierung der dort vorhandenen Komponenten haben. Das Konzept in den USA "Buy American" führt schon dazu, dass keine ...-Router mehr gekauft werden. Ich weiß nicht, wie der Stand dazu gerade in der Bundesrepublik ist. Damit haben wir weniger Austauschpunkte, weniger Abhörpunkte, an denen aber konzentriert Daten anfallen, und weniger Umgehungsmöglichkeiten. Die Frage ist, was rettet uns aus diesem Konzept, um diesen Raum der Freiheit zu behalten. Das Bundesverfassungsgericht hat in ständiger Rechtsrechung erklärt: Es braucht einen unbeobachteten Raum, in dem die Information, die Entscheidungsfindung und Willensbildung des Bürgers stattfinden kann, der nicht überwacht werden darf, da die Überwachung eine Verhaltensveränderung vornimmt, bzw. das Gefühl der Überwachung."
Andreas Lehner: "Wir finden es erfreulich, dass die Richter die Gelegenheit genutzt haben, um eine sehr grundsätzliche Aussage zu treffen. Durch das neue Grundrecht auf Gewährleistung der Vertraulichkeit und Integrität informationstechnischer Systeme wird ein Schutzbereich für die private Lebensführung im digitalen Zeitalter geschaffen." Quelle: "Ein erfreulicher Richterspruch", Süddeutsche Zeitung, 17.5.2010
30th Chaos Communication Congress (30C3), #5495, Hamburg, 16:00 Uhr, 30. Dezember 2013
After studying the various levels of activities that come together in BuggedPlanet and realizing the scope and level of implementation of NSA's SIGINT theatre, it's propably time to step back, summarize the big picture and ask how to handle it properly.
This talk will be structured in three parts:
Here I will give examples which SIGINT material is used in the form of Kompromat and Intelligence Operations to influence decisions and decision makers from various countries and continents to show
This part shall be a framework showing some ideas and principles to act, as well as necessary relationships to understand. The idea is to invite the audience to participate in this part and come up with ideas to create a broader concept and agree on the next steps.
30th Chaos Communication Congress (30C3), #5255, Hamburg, 14:00 Uhr, 30. Dezember 2013
From Stellar Wind to PRISM, Boundless Informant to EvilOlive, the NSA spying programs are shrouded in secrecy and rubber-stamped by secret opinions from a court that meets in a Faraday cage. The Electronic Frontier Foundation's Kurt Opsahl explains the known facts about how the programs operate and the laws and regulations the U.S. government asserts allows the NSA to spy on you.
The Electronic Frontier Foundation, a non-profit civil society organization, has been litigating against the NSA spying program for the better part of a decade. EFF has collected and reviewed dozens of documents, from the original NY Times stories in 2005 and the first AT&T whistleblower in 2006, through the latest documents released in the Guardian or obtained through EFF's Freedom of Information (government transparency) litigation.
EFF attorney Kurt Opsahl's lecture describes
and help you make sense of the many code names and acronyms in the news. He will also discuss the legal and policy ramifications that have become part of the public debate following the recent disclosures, and what you can do about it.
After summarizing the programs, technologies, and legal/policy framework in the lecture, the audience asked questions. See It Now - Season 4, Episode 18, 4 Jan. 1955 (on IMDb)
"Work is so hard and failure is -I guess- an unevitable condition of success."
(37 minutes, 27 seconds into the video) "The brain work darwinistic [not like a computer]." In Gerald Edelman's neurobiological model (Theory of Neuronal Group Selection, TNGS) our mind interacts with a relational data base. These 5 tenets determine this interaction.
I had been pretty isolated until 1986, partly perhaps because I... I wanted to be. I think I partly left England feeling that... that I was perhaps eccentric or would not fit well into the rigid... into the sort of rigid medical hierarchies in England, anymore than I would fit into the military. This was one of my reasons for leaving England. And after my training was complete in neurology in California, I... I wanted to move into a, sort of, hiding place. I... well, that's not a good way to put it. I hoped there might be interstices in medicine which I could occupy, untroubled by collegial criticism or contact. This was very much my situation at Beth Abraham Hospital. This was a... a poor, unknown chronic disease hospital, beneath the notice of neurologists, but in Beth Abraham I found my Awakenings patients and treasures galore, and I could spend as long as I liked with a patient. But I... I saw a few patients outside, the first one was Witty Ticcy Ray, and there were a few others.
But then after 1986 I had much more contact with... with colleagues, and Ralph introduced me to various visual colleagues of his, and I got a sense of the neuroscientific community. I didn't even know the word neuroscience in 1986, and obviously there had been a huge transformation since my physiology days at Oxford in the early '50s. At that time one knew almost nothing about the brain. Physiology stopped very much at the level of the spinal cord and the brain stem. People had no idea, for example, how perceptions were constructed, or the very sentence, 'perceptions are constructs', would have been meaningless... would not have conveyed anything in the 1950s. So, the whole... Ralph himself embodied a new neuroscientific reality and vision. As Crick did, of course, and he introduced me to many others, perhaps very especially a visual neuroscientist called Charles Gross, Charlie Gross, who was the first man to find cells in a monkey's brain which could respond specifically to the [sight of a] monkey's paw.
Robert Harris (book "The Ghost", screenplay), Roman Polanski (screenplay, director)
The clip sequence here does not reflect the sequence in the film. Also the film is more subtle, its composition is soft-spoken and gently touching.
Music Martha's Vineyard, Massachusetts, USA - In the holiday home (furniture from Walter Knoll) of his American publisher on the Atlantic island off New York, the successful and controversial former British Prime Minister has his memoirs written by a nameless ghost writer.
4.18 Andy, Concepts for global TSCM: getting out of surveillance state mode
4.19 Kurt Opsahl, Senior Staff Attorney, Electronic Frontier Foundation, Through a PRISM, Darkly: Everything we know about NSA Spying.
4.2 Ed Murrow: A Conversation with J. Robert Oppenheimer
"[The purpose of us -the Princeton Institute of Advanced Study- is] to help men who are creative and deep and active and struggling scholars and scientists, to get the job done that it is their destiny to do. This is a big order, and we take a corner of that, we do we best we can, we suffer from limits of money, of wisdom, of space. And we know if we get big, we will spoil everything, because the kind of intimacy, the kind of understanding, the kind of comradeship that is possible in a place of this size is hard to maintain in a place ten times as big. But we are here as an institution, I don't mean in our individual capacities. And as an institution we are here to take away from them the cares, the pleasures, that are their normal excuse for not following the rugged road of their own life and need and destiny."4.3 Gerald Edelman talks to Basil Gelpke: Simple words and deep meanings
4.4 Oliver Sacks: Isolation, feeling unique and visual neuroscience
4.5 The Ghost Writer
Cast: Ewan McGregor, Pierce Brosnan, Olivia Williams, Kim Cattrall, Tom Wilkinson, James Belushi, Jon Bernthal, Anna Botting, Tim Preece, Timothy Hutton, Morgane Polanski, Eli Wallach, Robert Pugh
Music: Alexandre Desplat
Director of photography: Pawel Edelman

5 Climate
5.1 Scientific Advisory Board of the German Federal Government "Global Environmental Changes" (WBGU)
World in Transition: Global Megatrends
Reinhold Leinfelder, Video-Seminar "Transformation", Global Megatrends (L02E01), 2012
Major source: Johan Rockström et al, Planetary Boundaries: Exploring the Safe Operating Space for Humanity, Ecology and Society, 2009
- Anthropocene: Earth no longer provides stable background for human activities. Man has become part of nature. We are massively changing the global environment. A constant annual growth means: annual growth = fixed fraction of current size (of economy). This produces exponential growth, and that was possible as long as the earth provided a stable background. i.e. one that was independent from human activities. But now, in the anthropocene, exponential growth soon leads to crises.
- "Emergeny plan necessary - time pressure: We have no low carbon model city, which would be a good model for others to follow or -may be- copy."
Amazingly, our government has just stifled the rapid growth of the renewable energies, contrary to the advice of the WBGU.
"2052: A Global Forecast for the Next Forty Years", written by Jorgen Randers (Co-Author of "The Limits to Growth", launched by the Club of Rome on May 7 2013), raises the issue that humankind as we know it will not survive on the planet if it continues on its path of over-consumption and short-termism."
To avoid collapse we might have to put up with a supra-national rather undemocratic government like we have in the EU and unlike the US has as federal government.
Humanity will not survive if it continues its waste and shortsightedness. That drastically the Club of Rome portrays the devastating consequences of climate change as a result of an unbreaked economic growth. 40 years after the "Limits of Growth" the thinktank warns us: Business as usual no longer is an option. Climate protection has to become profitable at last.
Expressed to the point, the reason for the decline of the West is the "triumph of financial capitalism". Missing in the calculation of the gross domestic product are environmental assetts such as water ressources, soil fertility, quality of life and a stable climate. In short: Profit calculation has to change.
Uwe Schneidewind, president of the Wuppertal Institute for Climate, Environment and Energy, said: "The 'incrusted' view on one's own economic growth might soon be criticised similarly as we criticise today the narrow value canon of the 1950s and 1960s. We will experience a substantial change of values from purely economic to sustainable thinking". "Our youth will no longer accept that such a narrow economic logic as we have experienced until now will continue to determine the actions of our governments. We will be surprised what power can emerge, similarly as we were surprised by the North African Spring."
Club-of-Rome-member Karl Wagner predicts a revolution in the 2020s - comparable with the one in 1848 against the feudal system. The culture of consumption will change direction to sustainable acting.
"Law enforcement is now attempting to broaden the Communications Assistance for Law Enforcement Act (CALEA) by requiring communications service providers to design their networks to make it easy and fast for law enforcement to perform wiretaps, pen-register, and trap-and-trace surveillance on a large number of people. In other words, the FBI wants service providers and equipment manufacturers to design their networks to be surveillance-friendly from the ground-up and starting at the product design phase. CALEA would then serve as a technology mandate, imposing design or architecture duties upon communications technology itself to "guarantee" that surveillance will always be fruitful. This is a far cry from simply requiring communications service providers to assist law enforcement in retrieving information or content that is reasonably available given the current state of technology." (Source, in cache)
6 May, 2013, re:publica, Berlin, 2013
"While the collection, storage and analysis of our data becomes ever cheaper and easier, governments around the world are eager to make the surveillance of citizens the default setting. Therefore, it has never been more important to explore countermeasures that would protect our fundamental right to privacy."
"While the European Union continues to take positive steps to ensuring that public and private bodies protect the privacy of citizens (for example through the Data Protection Regulation), much work remains to be done in addressing issues of due process in how governments use, protect, and request user data. Specifically, government requests for so-called "lawful access" to user data are trending in both democratic and non-democratic nations, presenting one of the greatest challenges for the protection of fundamental rights."
"This talk highlights this issue as well as provides a brief overview of the main challenges facing citizens in protecting their privacy, including some recent proposed laws in the EU and the US, that will show that bit by bit, our freedoms are being chipped away. The second half of the talk focusses on the need for domestic and international jurisprudence that protects our fundamental rights, and more broadly what can to be done to counter the surveillance state."
"From solutions such as Privacy by Design and expanding the use of privacy enhancing technologies, to the importance of transparency for both public and private actors, as well as how citizens can get involved and fight for the protection of their rights in the digital environment."
Source: 13.re:publica
6.1.2 Sign the People's Principles: End Mass Surveillance
Digital surveillance by world governments knows no bounds. Sign your name to the 'Necessary and Proportionate' Principles, and we'll deliver your petition to the United Nations, world leaders, and other policymakers who need to hear the voice of the people demanding an end to mass surveillance and a restoration of our human rights.
Sign the petition
6.2.1 Constanze Kurz, Frank Rieger, Comment of the Chaos Computer Club on Mandatory Data Retention, CCC, 9 July 2009
6.2.2 State Trojan "Contrary to all assurances of the responsible persons the trojan can continue to be seized, arbitrary code can be uploaded and the alleged "revision-secure logging" can be manipulated." "... In the reality of the trojan software an investigating authority can be mislead by a third party with fake "evidence". Already the first version of a self-made remote control software of the CCC has shown that the trojan is capable of receiving commands from an unauthorized third party, without the authorities noticing, let alone being able to revision-securely logging it." Ulf Buermeyer: Online-Search und Source-TKÜ [telecommunication surveillance of the source, i.e. a private computer] are allowed by the constitution according to the decision of the Federal Constitutional Court
6.3 Markus Beckedahl, Netzpolitik-Interview: Ulf Buermeyer about the State Trojan, 10 October 2011
. But one absolutely needs a special legal basis [see also: U. Buermeyer, When is the state allowed to enter the PC?
Limits to "Online-Searching" under Constitutional Law"]. This exists e.g. in [§ 20k of] German Federal Office of Criminal Investigation Law. For penal investigations -which we are dealing here with- there exists no law until now. Police law allows these intrusions only to avert future dangers, not to persecute past crimes.
netzpolitik.org: The Chaos Computer Club found a trojan on several hard drives that most probably were applied by security agencies. Is the introduction of such a trojan legal?
Ulf Buermeyer: Definitely not. Such software must never exist, and this is so because it allows input of data on the target system. The constitution does never allow this, as the Federal Constitutional Court ruled: Even an online search is only allowed to search, not to manipulate.
From an IT standpoint this judicial differentiation is hardly meaningful: the integrity of a system is severed as soon as software is introduced - regardless whether it can only read or also write. In this regard one can reasonably doubt whether introducing software can at all constitute a legal remote access.
netzpolitik.org: What are the clear limits under which the Federal Constitutional Court allowed conducting an online search?
Ulf Buermeyer: The Federal Constitutional Court saw the grave dangers originating from state operated surveillance software. It set up very high barriers: Only in case of a concrete danger for an "outstandingly important asset" are such measures possible. That means
Version: 30 April 2014
Address of this page
Jochen Gruber
Home